🔐 TekCERT System Requirements
- Microsoft.NET Framework v4.7.2.
Installing and Uninstalling
To install TekCERT, extract contents of TekCERT.zip to a temporary directory, run Setup.exe from the distribution.
Uninstall previous version if you upgrade from an earlier version
To uninstall TekCERT, double click TekCERT icon at "Add or Remove Programs" from Control Panel.
Running
If you familiar with X.509 certificates, the usage is very simple:
- Run TekCERT from Start / Program Files / TekCERT.
- Click "Generate Certificate" button to create the certificate after
filling necessary fields. You need to enter at least a valid "Name" for
the certificate. Generated certificates are located in "Local Computer/Personal"
store. You can also create certificate signing requests.
You can export public key in .cer (DER encoded X.509) format or with private key in .pfx format in after creating the certificate for client deployment. Click "Browse Certificates" tab, select the generated certificate and click "Export" button. You can list certificate under Local Computer or Machine store.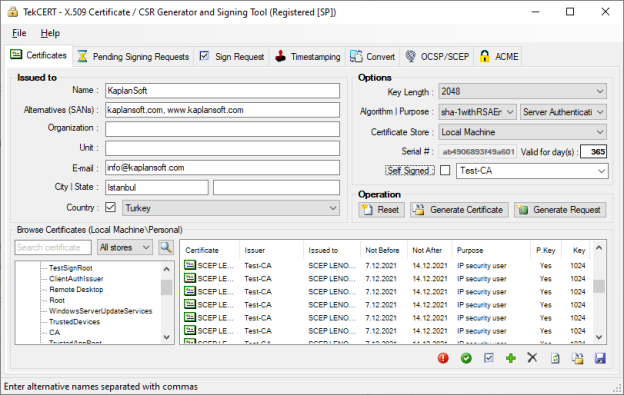
- You can select certificate store to import the signed certificate.
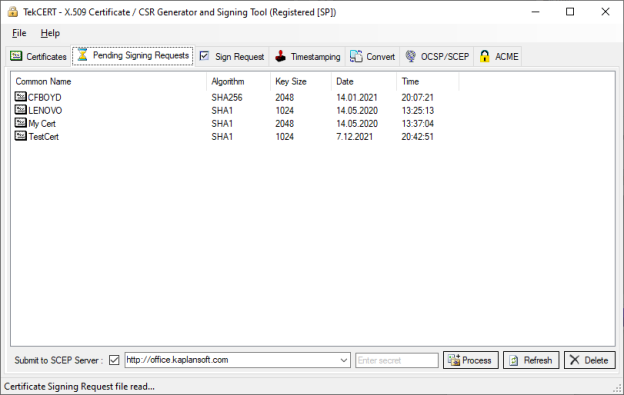
- You can browse pending requests and process received certificate authority responses in pending requests tab.
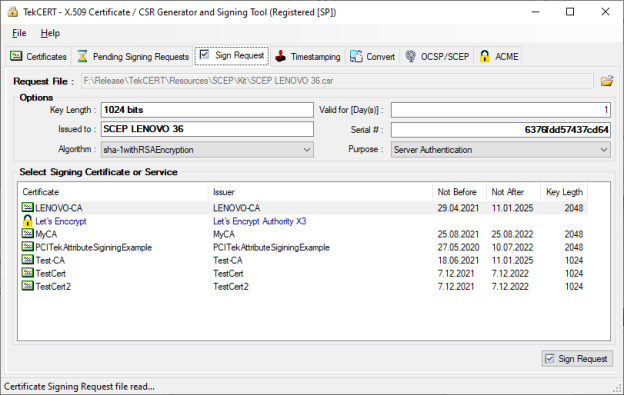
You can sign a certificate signing request using installed or generated CA certificates in the system.
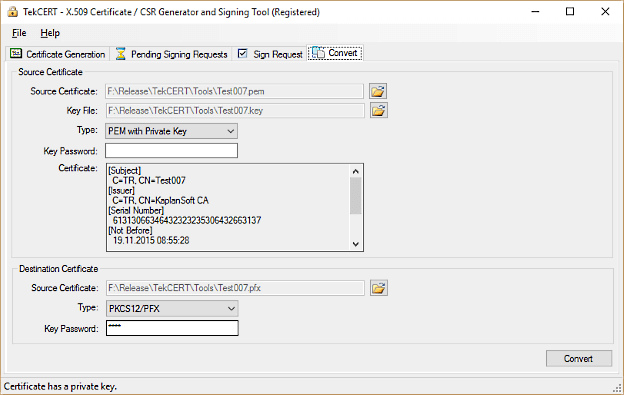
- You can convert various certificate types to each other.
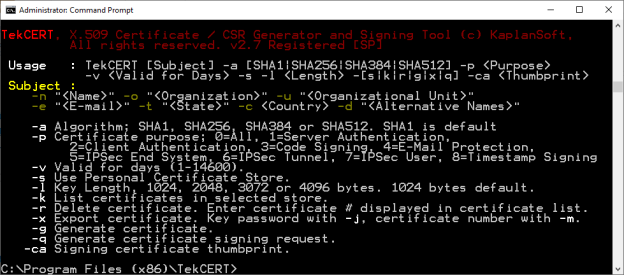
- Run TekCERT from the command line with -h parameter to see command line options. Open command line prompt as
shown below after clicking start button;
- Certificate generation example;
C:\Program Files (x86)\TekCERT>tekcert -g -a SHA1 -p 1 -v 365 -l 1024 -n "TestCert" -c US Certificate 'TestCert' is generated in Local Machine store.
TekCERT creates certificates with RSA key by default. Add -ECDSA parameter to create a certificate with ECDSA key. Valid key lengths are 256 (ECDsaP256), 384 (ECDsaP384) and 521 (ECDsaP521) for ECDSA.C:\Program Files (x86)\TekCERT>tekcert -g -a SHA1 -p 1 -v 365 -l 256 -n "TestCert" -c US -ECDSA
You can specify a specific CA certificate to sign the certificate;tekcert -g -a SHA1 -p 1 -v 365 -l 1024 -n "TestCert" -c US -ca "5776F320DD7A69ED913C5205F0BFD7AE7AF476BC"
TekCERT will submit certificate to be signed by an SCEP server if you specify the URL of SCEP responder service in the -ca parametertekcert -g -a SHA1 -p 1 -v 365 -l 1024 -n "TestCert" -c US -ca "http://office.kaplansoft.com"
You can specify SCEP secret by adding -ch parameter;tekcert -g -a SHA1 -p 1 -v 365 -l 1024 -n "TestCert" -c US -ca "http://office.kaplansoft.com" -ch "secret"
Sample certificate export;C:\Program Files (x86)\TekCERT>tekcert -x "cert.pfx" -m 9 -j "test" -s Selected certificate 'test' exported with its private key.
Sample private key export;C:\Program Files (x86)\TekCERT>tekcert -xp "private.key" -m 9 Private key of the selected certificate is exported in PKC#8 format.
- Run TekCERT from the command line with -ts parameter to see command line options for time stampting. Open command line prompt as
shown above after clicking start button. You can create timestamping requests, sign and verify them through the command line interface.
Timestamp request creation exampleC:\Program Files (x86)\TekCERT>tekcert -ts -cr -in "c:\Test\test.bin" -out "c:\output\request.tsq"
You can omit output file parameter. TekCERT will save timestamp request in to the same directory with source file with .tsq extension. This would be c:\Test\test.bin.tsq for the example above. You can add -ha option for hash algorithm to be used for message imprint calculation SHA-1, SHA-256 and SHA-512 algorithms are supported. Default is SHA-1.C:\Program Files (x86)\TekCERT>tekcert -ts -cr -in "c:\Test\test.bin" -out "c:\output\request.tsq" -ha sha256
You can also add certificate request field to force timestamping authorith to add public key of the signing certificate to timestamping response;C:\Program Files (x86)\TekCERT>tekcert -ts -cr -in "c:\Test\test.bin" -out "c:\output\request.tsq" -ha sha256 -cert
Timestamp request signing locallyC:\Program Files (x86)\TekCERT>tekcert -ts -sr -in "c:\output\request.tsq" -out "c:\output\response.tsr"
You can specify a timestamping certificate with -tsc option. Certificate thumbprint used to specify the certificate. TekCERT will use default or first available timestamping certificate if this parameter is omitted.
Timestamp request signing using a remote timestamping authorityC:\Program Files (x86)\TekCERT>tekcert -ts -sr -in "c:\output\request.tsq" -out "c:\output\response.tsr" -tss http://tsa.kaplansoft.com -u username -p password
TekCERT will try to sign request locally when -tsc or -tss options are not specified. Username and Passwords parameters are optional with -tss parameter. You can omit output file parameter for timestamp signing. TekCERT will save timestamp response in to the same directory with source file with .tsr extension. This would be c:\output\response.tsr for the example above.
Verifying timestamp signatureC:\Program Files (x86)\TekCERT>tekcert -ts -v "c:\output\response.tsr" -in "c:\output\request.tsq"
- in parameter is optional. TekCERT will just check timestamp response when original input file is not specified. - Please see TekCERT Manual for OCSP/SCEP server configuration and operation with Time Stamping functions.